February/2022 New Braindump2go PCCSE Exam Dumps with PDF and VCE Free Updated Today! Following are some new PCCSE Real Exam Questions!
QUESTION 96
A customer has configured the JIT, and the user created by the process is trying to log in to the Prisma Cloud console. The user encounters the following error message:
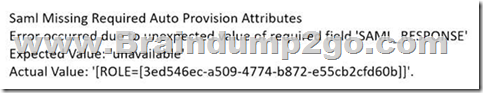
What is the reason for the error message?
A. The attribute name is not set correctly in JIT settings.
B. The user does not exist.
C. The user entered an incorrect password
D. The role is not assigned for the user.
Answer: A
Explanation:
Reference:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000CmZ4CAK
QUESTION 97
What are the two ways to scope a CI policy for image scanning? (Choose two.)
A. container name
B. image name
C. hostname
D. image labels
Answer: BD
Explanation:
Reference: https://www.optiv.com/insights/source-zero/blog/defending-against-container-threats-palo-alto-prisma-cloud
QUESTION 98
Which policy type in Prisma Cloud can protect against malware?
A. Data
B. Config
C. Network
D. Event
Answer: A
QUESTION 99
If you are required to run in an air-gapped environment, which product should you install?
A. Prisma Cloud Jenkins Plugin
B. Prisma Cloud Compute Edition
C. Prisma Cloud with self-hosted plugin
D. Prisma Cloud Enterprise Edition
Answer: B
Explanation:
Reference: https://docs.paloaltonetworks.com/prisma/prisma-cloud.html
QUESTION 100
What is the maximum number of access keys a user can generate in Prisma Cloud with a System Admin role?
A. 1
B. 2
C. 3
D. 4
Answer: B
QUESTION 101
An administrator needs to detect and alert on any activities performed by a root account.
Which policy type should be used?
A. config-run
B. config-build
C. network
D. audit event
Answer: C
QUESTION 103
A customer has multiple violations in the environment including:
– User namespace is enabled
– An LDAP server is enabled
– SSH root is enabled
Which section of Console should the administrator use to review these findings?
A. Manage
B. Vulnerabilities
C. Radar
D. Compliance
Answer: A
QUESTION 104
A customer has serverless functions that are deployed in multiple clouds. Which serverless cloud provider is covered be “overly permissive service access” compliance check?
A. Alibaba
B. GCP
C. AWS
D. Azure
Answer: C
Explanation:
Reference: https://docs.paloaltonetworks.com/prisma/prisma-cloud/prisma-cloud-admin-compute/compliance/serverless.html
QUESTION 105
A customer has a requirement to restrict any container from resolving the name www.evil-url.com. How should the administrator configure Prisma Cloud Compute to satisfy this requirement?
A. Choose “copy into rule” for any Container, set www.evil-url.com as a blocklisted DNS name in the Container policy and set the policy effect to alert.
B. Set www.evil-url.com as a blocklisted DNS name in the default Container runtime policy, and set the effect to block.
C. Choose “copy into rule” for any Container, set www.evil-url.com as a blocklisted DNS name, and set the effect to prevent.
D. Set www.evil-url.com as a blocklisted DNS name in the default Container policy and set the effect to prevent.
Answer: A
QUESTION 106
Which API calls can scan an image named myimage: latest with twistcli and then retrieve the results from Console?
A. $ twistcli images scan \
–address <COMPUTE_CONSOLE> \
–user <COMPUTER_CONSOLE_USER> \
–password <COMPUTER_CONSOLE_PASSWD> \
–verbose \
myimage: latest
B. $ twistcli images scan \
–address <COMPUTE_CONSOLE> \
–user <COMPUTER_CONSOLE_USER> \
–password <COMPUTER_CONSOLE_PASSWD> \
–details \
myimage: latest
C. $ twistcli images scan \
–address <COMPUTE_CONSOLE> \
–user <COMPUTER_CONSOLE_USER> \
–password <COMPUTER_CONSOLE_PASSWD> \
myimage: latest
D. $ twistcli images scan \
–address <COMPUTE_CONSOLE> \
–user <COMPUTER_CONSOLE_USER> \
–password <COMPUTER_CONSOLE_PASSWD> \
–console \
myimage: latest
Answer: B
Explanation:
Reference: https://docs.paloaltonetworks.com/prisma/prisma-cloud/prisma-cloud-admin-compute/tools/twistcli_scan_images
QUESTION 108
Which two of the following are required to be entered on the IdP side when setting up SSO in Prisma Cloud? (Choose two.)
A. Username
B. SSO Certificate
C. Assertion Consumer Service (ACS) URL
D. SP (Service Provider) Entity ID
Answer: BD
Explanation:
Reference: https://docs.paloaltonetworks.com/prisma/prisma-cloud/prisma-cloud-admin/manage-prisma-cloud-administrators/setup-sso-integration-on-prisma-cloud.html
QUESTION 109
An administrator sees that a runtime audit has been generated for a container.
The audit message is:
“/bin/ls launched and is explicitly blocked in the runtime rule. Full command: ls -latr”
Which protection in the runtime rule would cause this audit?
A. Networking
B. File systems
C. Processes
D. Container
Answer: D
Explanation:
Reference: https://docs.paloaltonetworks.com/prisma/prisma-cloud/21-04/prisma-cloud-compute-edition-admin/runtime_defense/runtime_audits.html
QUESTION 110
Which data security default policy is able to scan for vulnerabilities?
A. Objects containing Vulnerabilities
B. Objects containing Threats
C. Objects containing Malware
D. Objects containing Exploits
Answer: A
Explanation:
Reference: https://docs.paloaltonetworks.com/prisma/prisma-cloud/21-04/prisma-cloud-compute-edition-admin/vulnerability_management/vuln_management_rules.html
QUESTION 112
Which three fields are mandatory when authenticating the Prisma Cloud plugin in the IntelliJ application? (Choose three.)
A. Secret Key
B. Prisma Cloud API URL
C. Tags
D. Access Key
E. Asset Name
Answer: ABD
Explanation:
Reference: https://docs.paloaltonetworks.com/prisma/prisma-cloud/prisma-cloud-admin/prisma-cloud-devops-security/use-the-prisma-cloud-plugin-for-intellij.html
QUESTION 113
Which of the following are correct statements regarding the use of access keys? (Choose two.)
A. Access keys must have an expiration date
B. Up to two access keys can be active at any time
C. System Admin can create access key for all users
D. Access keys are used for API calls
Answer: BC
QUESTION 115
The development team is building pods to host a web front end, and they want to protect these pods with an application firewall.
Which type of policy should be created to protect this pod from Layer7 attacks?
A. The development team should create a WAAS rule for the host where these pods will be running.
B. The development team should create a WAAS rule targeted at all resources on the host.
C. The development team should create a runtime policy with networking protections.
D. The development team should create a WAAS rule targeted at the image name of the pods.
Answer: B
Explanation:
Reference: https://docs.paloaltonetworks.com/prisma/prisma-cloud/prisma-cloud-admin-compute/waas/waas-intro.html
QUESTION 116
A manager informs the SOC that one or more RDS instances have been compromised and the SOC needs to make sure production RDS instances are NOT publicly accessible.
Which action should the SOC take to follow security best practices?
A. Enable “AWS S3 bucket is publicly accessible” policy and manually remediate each alert.
B. Enable “AWS RDS database instance is publicly accessible” policy and for each alert, check that it is a production instance, and then manually remediate.
C. Enable “AWS S3 bucket is publicly accessible” policy and add policy to an auto-remediation alert rule.
D. Enable “AWS RDS database instance is publicly accessible” policy and add policy to an auto-remediation alert rule.
Answer: D
QUESTION 117
An administrator wants to enforce a rate limit for users not being able to post five (5) .tar.gz files within five (5) seconds.
What does the administrator need to configure?
A. A ban for DoS protection with an average rate of 5 and file extensions match on .tar.gz on WAAS
B. A ban for DoS protection with a burst rate of 5 and file extensions match on .tar.gz on CNNF
C. A ban for DoS protection with a burst rate of 5 and file extensions match on .tar gz on WAAS
D. A ban for DoS protection with an average rate of 5 and file extensions match on .tar.gz on CNNF
Answer: C
QUESTION 118
What is an automatically correlated set of individual events generated by the firewall and runtime sensors to identify unfolding attacks?
A. policy
B. incident
C. audit
D. anomaly
Answer: B
Explanation:
Reference: https://docs.paloaltonetworks.com/prisma/prisma-cloud/prisma-cloud-admin-compute/runtime_defense/incident_explorer.html
QUESTION 119
A customer wants to monitor the company’s AWS accounts via Prisma Cloud, but only needs the resource configuration to be monitored for now.
Which two pieces of information do you need to onboard this account? (Choose two.)
A. Cloudtrail
B. Subscription ID
C. Active Directory ID
D. External ID
E. Role ARN
Answer: AE
Explanation:
Reference: https://docs.paloaltonetworks.com/prisma/prisma-cloud/prisma-cloud-admin/connect-your-cloud-platform-to-prisma-cloud/onboard-your-aws-account/add-aws-organization-to-prisma-cloud.html
QUESTION 120
An administrator for Prisma Cloud needs to obtain a graphical view to monitor all connections, including connections across hosts and connections to any configured network objects. Which setting does the administrator enable or configure to accomplish this task?
A. ADEM
B. WAAS Analytics
C. Telemetry
D. Cloud Native Network Firewall
E. Host Insight
Answer: D
Explanation:
Reference: https://docs.paloaltonetworks.com/prisma/prisma-cloud/21-04/prisma-cloud-compute-edition-admin/firewalls/cnnf_self_hosted.html
QUESTION 121
Which two fields are required to configure SSO in Prisma Cloud? (Choose two.)
A. Prisma Cloud Access SAML URL
B. Identity Provider Issuer
C. Certificate
D. Identity Provider Logout URL
Answer: AB
Explanation:
Reference: https://docs.paloaltonetworks.com/prisma/prisma-cloud/prisma-cloud-admin/manage-prisma-cloud-administrators/setup-sso-integration-on-prisma-cloud/setup-sso-integration-on-prisma-cloud-for-microsoft-azure-active-directory.html
QUESTION 122
Which two IDE plugins are supported by Prisma Cloud as part of its DevOps Security? (Choose two.)
A. BitBucket
B. Visual Studio Code
C. CircleCI
D. IntelliJ
Answer: AC
Explanation:
Reference: https://docs.paloaltonetworks.com/prisma/prisma-cloud/prisma-cloud-admin/prisma-cloud-devops-security/prisma-cloud-plugins.html
QUESTION 123
Which two CI/CD plugins are supported by Prisma Cloud as part of its DevOps Security? (Choose two.).
A. BitBucket
B. Visual Studio Code
C. CircleCI
D. IntelliJ
Answer: CD
Explanation:
Reference: https://www.paloaltonetworks.com/blog/prisma-cloud/cloud-devops-plugins/
QUESTION 124
Given the following JSON query:
$.resource[*].aws_s3_bucket exists
Which tab is the correct place to add the JSON query when creating a Config policy?
A. Details
B. Compliance Standards
C. Remediation
D. Build Your Rule (Run tab)
E. Build Your Rule (Build tab)
Answer: C
Explanation:
Reference: https://docs.paloaltonetworks.com/prisma/prisma-cloud/prisma-cloud-policy-reference/configuration-policies/configuration-policies-build-phase/amazon-web-services-configuration-policies/policy_630d3779-d932-4fbf-9cce-6e8d793c6916.html
QUESTION 125
Which two attributes of policies can be fetched using API? (Choose two.)
A. policy label
B. policy signature
C. policy mode
D. policy violation
Answer: AD
Explanation:
Reference: https://docs.paloaltonetworks.com/prisma/prisma-cloud/prisma-cloud-admin/prisma-cloud-policies/create-a-policy.html
Resources From:
1.2022 Latest Braindump2go PCCSE Exam Dumps (PDF & VCE) Free Share:
https://www.braindump2go.com/pccse.html
2.2022 Latest Braindump2go PCCSE PDF and PCCSE VCE Dumps Free Share:
https://drive.google.com/drive/folders/1jrWPxXUTuYdqyaVCqz5y26glDCMUBtfZ?usp=sharing
3.2021 Free Braindump2go PCCSE Exam Questions Download:
https://www.braindump2go.com/free-online-pdf/PCCSE-PDF-Dumps(96-125).pdf
Free Resources from Braindump2go,We Devoted to Helping You 100% Pass All Exams!