July/2021 Latest Braindump2go 350-701 Exam Dumps with PDF and VCE Free Updated Today! Following are some new 350-701 Real Exam Questions!
QUESTION 311
What is a functional difference between a cisco ASA and a cisco IOS router with Zone-based policy firewall?
A. The Cisco IOS router with Zone-Based Policy Firewall denies all traffic by default, whereas the Cisco ASA starts out by allowing all traffic until rules are added
B. The Cisco IOS router with Zone-Based Policy Firewall can be configured for high availability, whereas the Cisco ASA cannot
C. The Cisco ASA can be configured for high availability whereas the Cisco IOS router with Zone- Based Policy Firewall cannot
D. The Cisco ASA denies all traffic by default whereas the Cisco IOS router with Zone-Based Policy Firewall starts out by allowing all traffic, even on untrusted interfaces.
Answer: D
QUESTION 312
A Cisco FTD engineer is creating a new IKEv2 policy called s2s00123456789 for their organization to allow for additional protocols to terminate network devices with. They currently only have one policy established and need the new policy to be a backup in case some devices cannot support the stronger algorithms listed in the primary policy.
What should be done in order to support this?
A. Change the integrity algorithms to SHA* to support all SHA algorithms in the primary policy
B. Make the priority for the new policy 5 and the primary policy 1.
C. Change the encryption to AES* to support all AES algorithms in the primary policy
D. Make the priority for the primary policy 10 and the new policy 1
Answer: D
QUESTION 313
Which cloud model is a collaborative effort where infrastructure is shared and jointly accessed by several organizations from a specific group?
A. private
B. hybrid
C. community
D. public
Answer: C
QUESTION 314
A customer has various external HTTP resources available including Intranet Extranet and Internet, with a proxy configuration running in explicit mode.
Which method allows the client desktop browsers to be configured to select when to connect direct or when to use the proxy?
A. Transport mode
B. Forward file
C. PAC file
D. Bridge mode
Answer: A
QUESTION 315
An organization uses Cisco FMC to centrally manage multiple Cisco FTD devices. The default management port conflicts with other communications on the network and must be changed. What must be done to ensure that all devices can communicate together?
A. Set the sftunnel to go through the Cisco FTD
B. Change the management port on Cisco FMC so that it pushes the change to all managed Cisco FTD devices
C. Set the sftunnel port to 8305
D. Manually change the management port on Cisco FMC and all managed Cisco FTD devices
Answer: B
QUESTION 316
Refer to the exhibit. What does this python script accomplish?
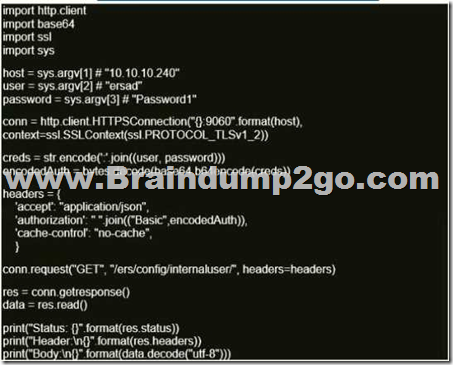
A. It lists the LDAP users from the external identity store configured on Cisco ISE
B. It authenticates to a Cisco ISE server using the username of ersad
C. It allows authentication with TLSv1 SSL protocol
D. It authenticates to a Cisco ISE with an SSH connection
Answer: C
QUESTION 317
Which component of cisco umbrella architecture increases reliability of the service?
A. Anycast IP
B. AMP Threat grid
C. Cisco Talos
D. BGP route reflector
Answer: D
QUESTION 318
An organization wants to use Cisco FTD or Cisco ASA devices Specific URLs must be blocked from being accessed via the firewall, which requires that the administrator input the bad URL categories that the organization wants blocked into the access policy.
Which solution should be used to meet this requirement?
A. Cisco ASA because it enables URL filtering and blocks malicious URLs by default, whereas Cisco FTD does not
B. Cisco ASA because it includes URL filtering in the access control policy capabilities whereas Cisco FTD does not.
C. Cisco FTD because it includes URL filtering in the access control policy capabilities whereas Cisco ASA does not.
D. Cisco FTD because rt enables URL filtering and blocks malicious URLs by default, whereas Cisco ASA does not
Answer: D
QUESTION 319
Which type of DNS abuse exchanges data between two computers even when there is no direct connection?
A. malware installation
B. command-and-control communication
C. network footprinting
D. data exfiltration
Answer: A
QUESTION 320
Which DevSecOps implementation process gives a weekly or daily update instead of monthly or quarterly in the applications?
A. orchestration
B. CI/CD pipeline
C. container
D. security
Answer: B
QUESTION 321
An organization deploys multiple Cisco FTD appliances and wants to manage them using one centralized solution. The organization does not have a local VM but does have existing Cisco ASAs that must migrate over to Cisco FTDs.
Which solution meets the needs of the organization?
A. Cisco FMC
B. CSM
C. Cisco FDM
D. CDO
Answer: B
QUESTION 322
An administrator configures a Cisco WSA to receive redirected traffic over ports 80 and 443.
The organization requires that a network device with specific WSA integration capabilities be configured to send the traffic to the WSA to proxy the requests and increase visibility, while making this invisible to the users.
What must be done on the Cisco WSA to support these requirements?
A. Configure transparent traffic redirection using WCCP in the Osco WSA and on the network device
B. Configure active traffic redirection using WPAD m the Cisco WSA and on the network device
C. Use the Layer 4 setting in the Cisco WSA to receive explicit forward requests from the network device
D. Use PAC keys to allow only the required network devices to send the traffic to the Cisco WSA
Answer: A
QUESTION 323
An organization configures Cisco Umbrella to be used for its DNS services. The organization must be able to block traffic based on the subnet that the endpoint is on but it sees only the requests from its public IP address instead of each internal IP address.
What must be done to resolve this issue?
A. Set up a Cisco Umbrella virtual appliance to internally field the requests and see the traffic of each IP address
B. Use the tenant control features to identify each subnet being used and track the connections within the Cisco Umbrella dashboard
C. Install the Microsoft Active Directory Connector to give IP address information stitched to the requests m the Cisco Umbrella dashboard
D. Configure an internal domain within Cisco Umbrella to help identify each address and create policy from the domains
Answer: D
QUESTION 324
An organization wants to secure data in a cloud environment Its security model requires that all users be authenticated and authorized. Security configuration and posture must be continuously validated before access is granted or maintained to applications and data. There is also a need to allow certain application traffic and deny all other traffic by default.
Which technology must be used to implement these requirements?
A. virtual routing and forwarding
B. microsegmentation
C. access control policy
D. virtual LAN
Answer: C
QUESTION 325
Why is it important to implement MFA inside of an organization?
A. To prevent man-the-middle attacks from being successful.
B. To prevent DoS attacks from being successful.
C. To prevent brute force attacks from being successful.
D. To prevent phishing attacks from being successful.
Answer: C
QUESTION 326
How does Cisco Workload Optimization Manager help mitigate application performance issues?
A. It deploys an AWS Lambda system
B. It automates resource resizing.
C. It optimizes a flow path
D. it sets up a workload forensic score
Answer: B
QUESTION 327
An engineer adds a custom detection policy to a Cisco AMP deployment and encounters issues with the configuration. The simple detection mechanism is configured, but the dashboard indicates that the hash is not 64 characters and is non-zero. What is the issue?
A. The hash being uploaded is part of a set in an incorrect format
B. The file being uploaded is incompatible with simple detections and must use advanced detections
C. The engineer is attempting to upload a hash created using MD5 instead of SHA-256
D. The engineer is attempting to upload a file instead of a hash
Answer: C
QUESTION 328
What is a benefit of using telemetry over SNMP to configure new routers for monitoring purposes?
A. Telemetry uses a pull, method which makes it more reliable than SNMP
B. Telemetry uses push and pull, which makes it more scalable than SNMP
C. Telemetry uses a push method which makes it faster than SNMP
D. Telemetry uses push and pull which makes it more secure than SNMP
Answer: B
QUESTION 329
An organization wants to provide visibility and to identify active threats in its network using a VM. The organization wants to extract metadata from network packet flow while ensuring that payloads are not retained or transferred outside the network.
Which solution meets these requirements?
A. Cisco Umbrella Cloud
B. Cisco Stealthwatch Cloud PNM
C. Cisco Stealthwatch Cloud PCM
D. Cisco Umbrella On-Premises
Answer: A
QUESTION 330
What is a difference between GETVPN and iPsec?
A. GETVPN provides key management and security association management.
B. GETVPN reduces latency and provides encryption over MPLS without the use of a central hub.
C. GETVPN is based on IKEv2 and does not support IKEv1.
D. GETVPN is used to build a VPN network with multiple sites without having to statically configure all devices
Answer: C
QUESTION 331
An administrator configures a new destination list in Cisco Umbrella so that the organization can block specific domains for its devices.
What should be done to ensure that all subdomains of domain.com are blocked?
A. Configure the *.com address in the block list.
B. Configure the *.domain.com address in the block list
C. Configure the *.domain.com address in the block list
D. Configure the domain.com address in the block list
Answer: C
QUESTION 332
An organization wants to secure users, data and applications in the cloud.
The solution must be API-based and operate as a cloud-native CASB.
Which solution must be used for this implementation?
A. Cisco Firepower Next-Generation Firewall
B. Cisco Cloud Email Security
C. Cisco Umbrella
D. Cisco Cloudlock
Answer: D
QUESTION 333
Which attribute has the ability to change during the RADIUS CoA?
A. NTP
B. authorization
C. accessibility
D. membership
Answer: A
QUESTION 334
What is a difference between an XSS attack and an SQL injection attack?
A. SQL injection is a hacking method used to attack SQL databases, whereas XSS attacks can exist in many different types of applications
B. XSS is a hacking method used to attack SQL databases, whereas SQL injection attacks can exist in many different types of applications
C. SQL injection attacks are used to steal information from databases whereas XSS attacks are used to redirect users to websites where attackers can steal data from them
D. XSS attacks are used to steal information from databases whereas SQL injection attacks are used to redirect users to websites where attackers can steal data from them
Answer: C
QUESTION 335
Configure the Cisco ESA to modify policies based on the traffic seen.
What is a benefit of conducting device compliance checks?
A. It indicates what type of operating system is connecting to the network.
B. It validates if anti-virus software is installed.
C. It scans endpoints to determine if malicious activity is taking place.
D. It detects email phishing attacks.
Answer: B
QUESTION 336
Refer to the exhibit. How does Cisco Umbrella manage traffic that is directed toward risky domains?
A. Traffic is managed by the application settings, unhandled and allowed
B. Traffic is allowed but logged
C. Traffic is managed by the security settings and blocked.
D. Traffic is proxied through the intelligent proxy
Answer: C
QUESTION 337
An administrator is establishing a new site-to-site VPN connection on a Cisco IOS router.
The organization needs to ensure that the ISAKMP key on the hub is used only for terminating traffic from the IP address of 172.19.20.24.
Which command on the hub will allow the administrator to accomplish this?
A. crypto ca identity 172.19.20.24
B. crypto isakmp key CiscoOl23456789 172.19.20.24
C. crypto enrollment peer address 172.19.20.24
D. crypto isakmp identity address 172.19.20.24
Resources From:
1.2021 Latest Braindump2go 350-701 Exam Dumps (PDF & VCE) Free Share:
https://www.braindump2go.com/350-701.html
2.2021 Latest Braindump2go 350-701 PDF and 350-701 VCE Dumps Free Share:
https://drive.google.com/drive/folders/1Fz2rtzfDdCvomlIPqv3RZzNAkMIepErv?usp=sharing
3.2021 Free Braindump2go 350-701 Exam Questions Download:
https://www.braindump2go.com/free-online-pdf/MS-203-PDF-Dumps(219-231).pdf
https://www.braindump2go.com/free-online-pdf/MS-203-VCE-Dumps(206-218).pdf
Free Resources from Braindump2go,We Devoted to Helping You 100% Pass All Exams!